Deliverability
Protecting your domain reputation with DMARC
Deliverability

As someone who works in this wonderful world of email, I can tell you there are a few things that just make life miserable for everyone: spammers and phishers. The interwebz is still the preferred platform for business and social interactions, so of course, there’s more incentive for bad actors to target users for their own financial gain. Let’s look at the stupid easy ways bad actors can lure us into a trap, and how we can stop getting pwned by spammers.
DMARC is the lesser known authentication. If you’re in the email game, then it’s more likely that you’ve embraced DKIM and SPF. Though it’s very effective – having stopped more than 90 million phishing attacks in the first half of 2022 alone, DMARC is still not widely adopted. With over 90% of cyber attacks beginning with phishing (the very thing DMARC defends against), this is the security protocol you don’t want to sleep on.
DKIM and SPF are great for indicating where messages should be coming from, though not vmany ISPs filter email using these authentications alone. Both DKIM and SPF provide the mechanics to filter out messages that fail their checks, but most providers will still allow message to go through. This is because it’s really hard to tell how many legitimate emails are being sent that don’t authenticate – especially if the sender isn’t getting any feedback. This is where DMARC comes in.
DMARC (Domain-based Message Authentication, Reporting & Conformance) uses both the SPF and DKIM records together to better identify who sent the message. It can tell you if the sender had permissions to send and identify themselves as the domain in the “From” field of your email header.
Sender Policy Framework (SPF) is controlled at the DNS level. It’s where you can say which servers can send on your behalf, and lets you reference whether the originating IP matches the list on your DNS. A matching IP is how the recipient server knows the message is coming from an authorized sender of your domain.
DomainKeys Identified Mail (DKIM) signs your messages to signal that it has been sent from the server that created the message, and not from an imposter that intercepted the message and inserted something into the message body itself.
To pass DMARC checks, SPF or DKIM must meet the requirements of both alignment and authentication. There must be alignment between the domain in the “from” address, and the domain identified in the return path or “d=” portion of the DKIM signature.
If you’re looking for more resources on DMARC, the DMARC site provides suggestions for aggregation services that take that return data and display it for you in a nice way that humans can read. Because who doesn’t like a solid feedback loop that helps to improve email deliverability?
We’re big fans of DMARC both in terms of security and deliverability. It’s one thing to talk about the logistics, but what are some examples of the risks that DMARC helps prevent?
One of the easiest ways for bad actors to infiltrate our lives is to use our trusting – and often lax – attitude towards established senders. Email spoofing tests our trust and exploits it, using it against us to see if we’ll take the bait if it looks like a message is coming from someone we know. You can be on the receiving end and not know the difference because bad actors will mimic email headers to look legitimate.
More sophisticated spoofing attacks will often include company logos, be well written, and have links to websites that also look legitimate, making it really hard for a user to realize that they are being phished until it’s too late. But if you take a closer look at the full details of your email header, you can catch the weird things like IP addresses that you didn’t authorize to send on your behalf. It’s all too easy to replicate an email header and put your domain reputation at risk.
An unprotected domain is bad news for your reputation with ISPs. Your own domain users are left vulnerable to phishing attacks where bad actors will trick recipients with personalized messages. These messages can attempt to gain passwords, payment information, or confidential company information that you would not normally share. So, if you can’t function without binge watching Futurama, and Netflix is threatening to cancel your account because of a problem with your billing information…I’d say
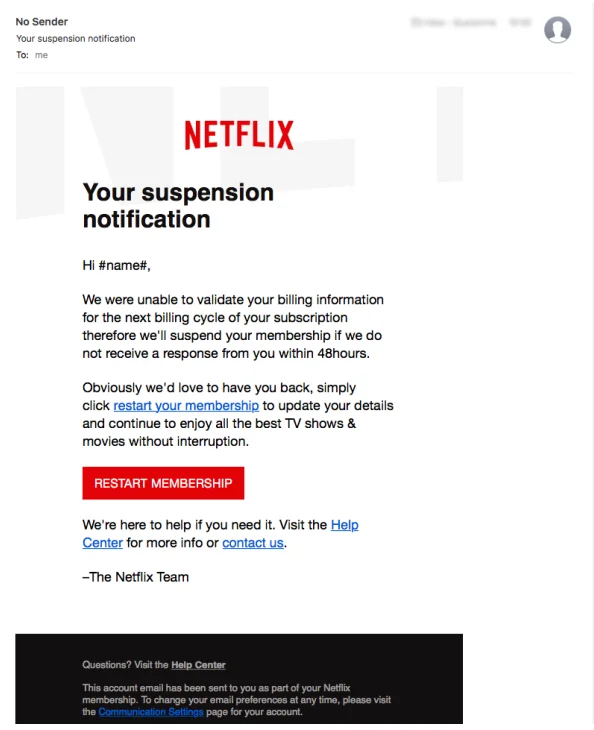
And that’s just the small stuff. These attacks are the Moby Dick of ‘phising’– just a security disaster waiting to happen because of how far they reach and the size of their impact. They can hit your organization in the form of a message sent from a senior executive or a high-profile contact and are made to look like official correspondence. It’s pretty much a message you would reasonably expect like a legal subpoena, customer complaint, or a message from the CEO. If you’re being asked to provide confidential information or direct payment to an obscure source…flag it immediately.
DMARC is by no means a magic wand that will eliminate spoofing of your domain, but it can deter a spammer or phisher from using your domain name while trying to execute one of these attacks. And of course, it can also help protect your domain reputation by validating your identity and separating your sending actions from a spammer who is trying to mimic you.
To protect your own users from spoofing attacks, remember that DMARC is part of the toolset that you will need , but user education is key.. To dive deeper into learning about reputation protection, check out our webinar on all things dedicated IP and learn when to use them for email.
Deliverability is a challenging topic. DMARC is one piece of the authentications that secure your email program, but it’s still only the tip of the iceberg.