Product
Security success story: How Mailgun stopped a large-scale phishing attack
Product

When you support companies around the world by facilitating the sending of billions of emails, you’ve got a pretty big target on your back. So, we expect threat actors to take aim at us. This summer, Sinch Mailgun and other companies in the digital communications space became the targets of a large-scale multi-channel phishing attack.
First, here’s the good news…
Mailgun was effectively able to mitigate this phishing attack and the bad actors failed to impact our systems in any way. To be clear, that means no customer accounts or data were compromised.
The only bad news is that we can expect these kinds of threats to continue and will only become more sophisticated with time. But that’s okay, because we’re ready for it.
So, how did we stop this large-scale phishing attack? To help you understand the measures Mailgun takes to protect our platform as well as our customers, we decided to give you a look behind the scenes of a cybersecurity response in our organization. The story begins in late July when employees started getting suspicious SMS messages.
The first phishing attempts occurred on July 23rd when multiple employees received malicious text messages alerting them to a change in their schedules. These messages, sent from an unknown number, implied they were coming from Sinch, which is the new parent company of Mailgun, Mailjet, and Email on Acid.
The first thing that stands out about this attack is that it used SMS phishing, also known as smishing. As the attack progressed, the threat actors also attempted to phish employees via vishing (voice/phone call phishing).
Maybe the attackers thought phishing an email service provider (ESP) through the inbox was a little too obvious. Whatever the case, while smishing and vishing aren’t nearly as common as traditional email phishing, they are definitely on the rise.
According to Proofpoint’s “State of the Phish Report,” 74% of companies around the world experienced smishing attacks last year, and 69% saw vishing attacks. Both statistics represent a double-digit increase for these threat vectors year-over-year.
Here’s a look at how the smishing messages appeared to Mailgun employees.
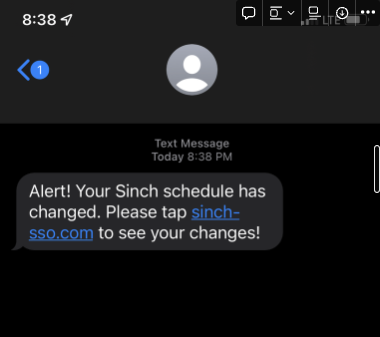
Phishers often use a sense of urgency to convince targets to click on links that take them to fake login pages. In this case, the domain name for the fake login page wouldn’t be familiar to our employees.
However, the attackers tried various messages, using the name of different identity management systems in the link as well as different calls to action, such as expired passwords.
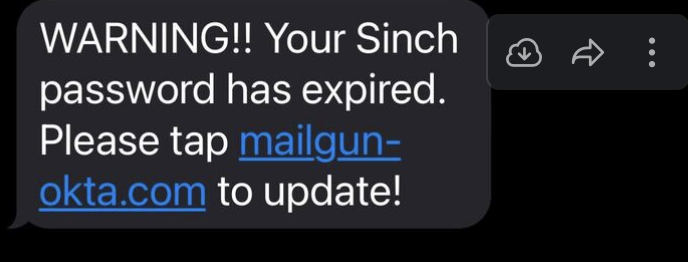
Phishing attempts like this can be quite convincing. But as you’ll see, this particular phishing attack didn’t fool our security savvy employees or Mailgun’s sophisticated security measures.
Another interesting factor in this attack is that it occurred on the personal devices of employees. This may have been an attempt to get around Mailgun’s internal threat detection technology. But Sinch and Mailgun do not typically contact people this way, so it raised red flags among our employees.
Still, you might wonder how the threat actors got the personal contact information of our employees in the first place. Was it leaked somewhere? The answer is Open-Source Intelligence (OSINT) gathering, which is a key component of social engineering attacks.
Using OSINT, bad actors gather publicly available information about people and organizations from around the web and build profiles about them. For example, they could discover someone’s place of employment and their cell phone number just from scraping a LinkedIn page.
Keep in mind that this typically doesn’t happen manually. Threat actors use automated software to gather large amounts of information quickly as well as to send malicious messages. That’s what makes a large-scale phishing attack possible – even simple.
Here’s what would have happened had any of our employees followed through with all the steps the threat actors were trying to persuade them to take. Again… this never actually happened. Instead, the Mailgun Security team utilized a sandbox environment to investigate the motives and methods of the attack.
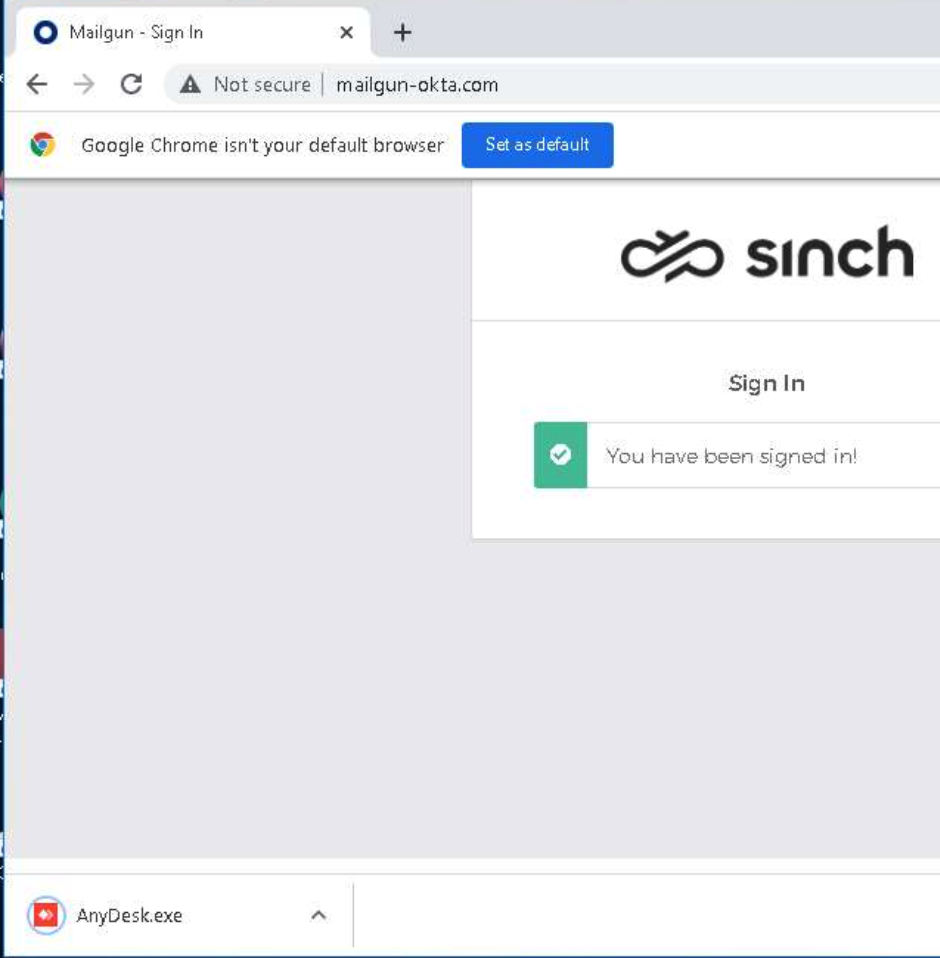
After clicking the link in the SMS message, targets land on a fake login page that looks like this:
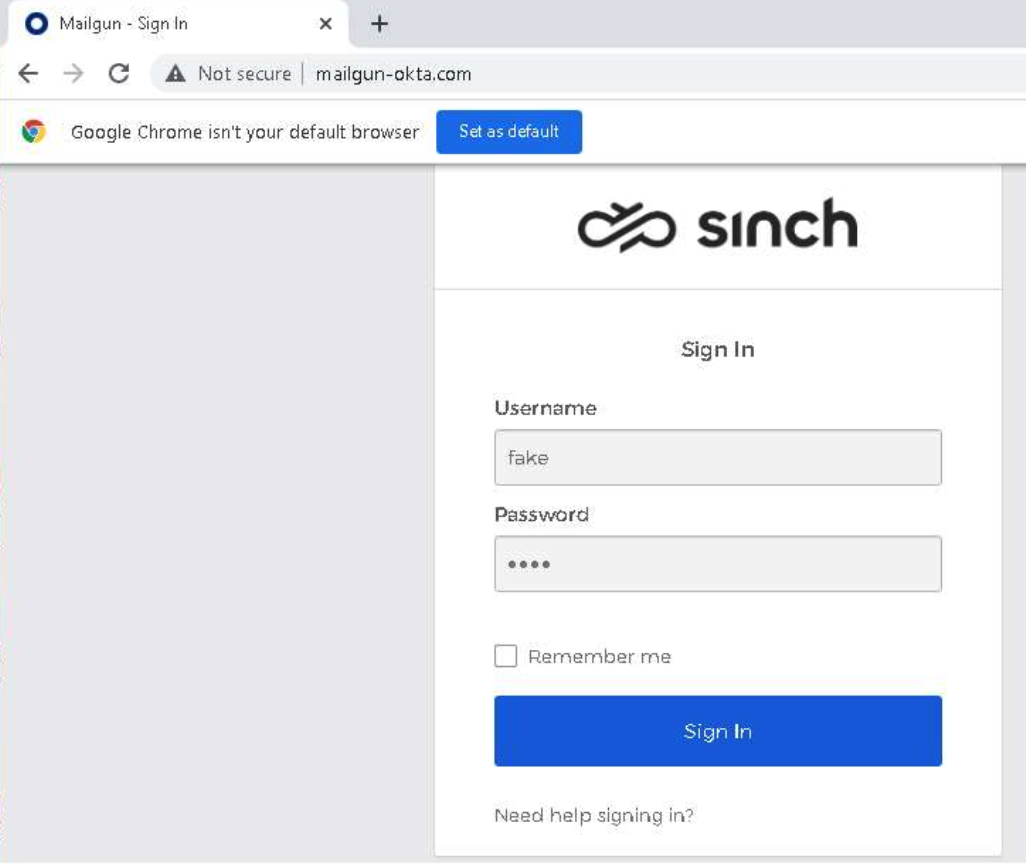
The design of login pages is usually very easy to replicate because they’re simple pages with a few basic elements. So, they may look convincing, but there’s one major sign of trouble here. Notice that the Chrome browser indicates this page is “Not secure.” That would almost never be the case on a real Okta login page.
These phishing sites replicated or proxied legitimate Okta login pages to the end user. There, it would attempt to obtain the target’s username and password. If that happened, the password would be compromised.
After entering their credentials, the target would see a page on which they were asked to enter a token or temporary login. That was another red flag for employees because Mailgun does not use Time-based One Time Passwords (TOTPs).
Hypothetically, if a user had gone through the process, they would have seen a “Success” page and a malicious executable would be downloaded onto their device. As you can see in the screenshot below, the executable was a piece of software called AnyDesk.exe.
Had the software run, the software would allow the attacker to gain remote access to the user’s machine/device. But just to reiterate: This never happened to any Mailgun employee. Next, let’s take a closer look at how and why we avoided trouble in this large-scale phishing attack.
At first, the attack seemed somewhat sophisticated. But as we triaged and investigated the situation, it became clear that this was a fairly typical OSINT attack that also targeted other companies in our industry. Still, it had the potential to do some damage, and we were glad Mailgun had the right security controls in place.
Mailgun is constantly training employees, alerting them to new threats, and sending out phishing simulations so that security stays top of mind. Security isn’t an afterthought here. It is engrained in company culture, and in this case, it really paid off.
We have technology in place to dramatically limit the number of phishing attempts that get through to Mailgun employees. The vast majority of phishing emails never even make it to a user’s inbox. But our reach is more limited when bad actors target personal devices. In this attack, there were even family members of employees who received smishing messages.
Given these attacks were targeted at personal devices, the fact that employees noticed and promptly reported these smishing attempts to the Mailgun Security team was integral to us responding quickly and efficiently. We alerted the entire company to the threat on multiple communication channels.
Employees also helped spread the word, and everyone remained vigilant against anything that looked suspicious. At Mailgun, we have a culture of transparency and trust. Our users are trained to report a potential or true security incident, without fear of punishment.
While employee awareness was essential, arguably the most important protection involved is hardware keys leveraging what’s known as the FIDO2 protocol (Fast Identify Online). These hardware keys perform origin checking, which means it could tell that the Okta login pages were not legitimate. If the domain in the browser’s address bar doesn’t match the domain used in the data sent between the real domain and the hardware key, the login attempt fails. So, these keys effectively eliminate the possibility of using so-called Man-in-the-Middle (MitM) attacks against our company.
Put simply, Mailgun uses YubiKeys for user authentication. These are physical hardware tokens that are required before access to our software and systems is granted. Even if the hackers get someone’s credentials, they can’t use it to login without the hardware key.

YubiKey hardware tokens from Yubico
Companies implementing hardware keys with the FIDO2 protocol are able to mitigate the impact of credential compromise campaigns. That’s because threat actors need the physical key to be present in order to gain any access.
Speaking of domains, Mailgun also worked with domain registrars to request domain takedowns and have these phishing sites pooled as malicious. That means even if our someone from Mailgun did click a link in a smishing message, the fake websites would no longer be active.
In addition to the two important protections mentioned already, Mailgun implements a multi-layered approach to product security that provides protection in case a safeguard (or human) fails.
For example, had any of these attack attempts s쳮ded in delivering the malicious file, our endpoint detection and response software would have immediately quarantined it as malware before it could run on the end-user’s device.
As our team investigated any potential impact of the phishing attempt, we leveraged multiple tools that aggregate and correlate login attempts. This helped us to quickly identify users who may have entered credentials, but the login was blocked or failed because of multifactor authentication.
We also leveraged the specific indicators of compromise for this attack and set up alerting. While we already have these alerting systems in place, we then tailored them to match the specific signals connected to this large-scale phishing attack. That means, if we see real-time user authentication failures, as well as other indicators of suspicious account activity, we can quickly address and investigate whether an individual had been impacted.
Here are a few important points from Mailgun’s response to this phishing attack that you can apply to your own security strategy:
Threat actors often use psychology and the propensity for humans to make mistakes to their advantage. You’re only strong as your weakest link. A workforce that’s well-educated on potential security threats is less likely to miss warning signs.
A widespread phishing attack can be fast and furious. You need ways to quickly and effectively disseminate information about the attack. That should include communication channels such as email, chat applications, company intranet alerts, and even company-wide meetings. You also need places and a simple procedure for people to report potential security incidents (dedicate email address or Slack channel).
As phishing becomes more sophisticated, bad actors are finding ways around simple multi-factor authentication. Hardware tokens and biometric security measures leveraging the FIDO2 protocol make it much more difficult to gain access, even when credentials are compromised.
Don’t rely on one or two protections alone. Always have a Plan B (or C, D, and E) so that threat actors will find their attacks blocked even if they get around other security measures.
Ensure you have proper technologies in place that have visibility across the enterprise. Being able to quickly detect, correlate, and identify potentially malicious activities is critical to a success response effort.
While our security team discovered some information about the source of this large-scale phishing attack, we still aren’t sure exactly who was behind it. We do know that we are a popular target because we serve high-profile customers who send email to people all over the world.
If it’s not clear already, we take security very seriously at Sinch Mailgun. We also have a culture of complete transparency that extends beyond our employees. One of the reasons we’re publishing this article is to let you know what has happened and show you how we respond to and investigate these potential security situations.
Mailgun always learns from activities like this, and we continually take steps to mature our security posture, increasing our cyber resiliency. As these things continue to happen, we’re taking an agile approach to implement additional technology to make sure we’re protecting our customers, platform, and employees.
We will continue to invest in technology to help us detect threats, protect our customers, and respond to anything the bad guys throw at us. To find out more, visit the Mailgun Security Portal where you can view or request access to documents detailing our methods as well certifications and audits that prove we provide the highest level of protection.
Social engineering and intelligence