IT & Engineering
What is single sign-on and how does it work?
Single sign-on (SSO) is a one-stop solution for a multi-access problem. Unsurprisingly, there’s a lot going on behind the scenes. From identity providers to authorization protocols, we’re covering everything that goes into SSO solutions, and what they can do for you.
PUBLISHED ON
Single sign-on is the “one ring to rule them all” of internet security. One ring to find them, one ring to bring them all, and bind the other rings through Identity and Access Management (IAM).
Another – less geeky – way to look at it is as a signal of scalability that attracts clients to your application. Why? SSO reduces friction from the very first step – sign up.
Adding SSO to your software or application can be an involved process. In this post, we’ll guide you through the landscape of SSO, and answer some of your burning questions. How does SSO work? What security protocols can you use? And what’s the importance of SSO anyway?
Table of contents
OAuth 2.0
OpenID Connect
SSO pros
SSO cons
Okta
Auth0
OneLogin
Remote/hybrid SaaS companies
Companies with extensive technology stacks
What is SSO?
It’s a cry for help at sea. Oh wait...that’s SOS.
SSO is an authentication scheme that enables users to log into multiple applications using a single set of login credentials. It’s a great choice for companies because centralizing authentication processes not only increases security but makes it easier to monitor and maintain. With one complex password, users can log into multiple services from a single platform, eliminating password fatigue; the creation of multiple passwords that need to be securely stored or remembered.
How does SSO work?
Great question.
Single sign-on is a method of user authentication, and works by sharing and validating login credentials between service providers. Instead of remembering passwords to all your accounts, you can link those accounts to an SSO provider. SSO implementation can be as easy as signing up for a service. With a single SSO login point, you gain secure access to all the subscriptions and applications which have been configured.
If you think about it, SSO isn’t a stand-alone protocol that you insert into your login process as much as it is an independent service with its own database and infrastructure that you integrated with. Single sign-on solutions (also known as identity providers, or IdPs) build a relationship of trust with service providers (SPs) – that is you, or other web-based applications – by keeping the integrity of messages between a service and an identity provider secure using certificates and public key cryptography.

Authentication and authorization protocols
Identity management is great but now we need a way to get login data from point A to point B.
IdPs need a secure way to transmit data. Security Assertion Markup Language (SAML 2.0) is an authentication framework for exchanging identity information between online partners. This is an open standard, which means it’s publicly available and maintained collaboratively by developers around the world.
SAML solves a few key problems for an IdP:
Provides a single point of authentication (only sent to IdP directly).
Does not require user credentials to by synchronized between directories.
User credentials need to be securely stored and transferred between an IdP and a service. SAML 2.0 is an XML-based framework that manages this data transfer. The user’s browser plays a central role in this exchange of information. Here’s how SAML 2.0 typically works:
The user has an IdP (e.g., Okta).
The user logs into a web application, such as a CRM, from a browser.
The application generates a SAML request.
The SSO provider (Okta) parses the request to authenticate the user’s credentials.
If the user is not already logged into the SSO platform, the SSO provider prompts the user to log in using their SSO credentials, otherwise this step is skipped.
Once logged in, the SSO provider generates a SAML response and sends it back to the application through the user’s browser.
The application verifies the response using the IdP’s public certificate and logs the user in.
The most known protocol supporting SSO is SAML 2.0, but this isn’t the only option. When reviewing options there are two big things to keep in mind. First, whether a company decides to use your application may boil down to the way you integrate with their infrastructure. Second, you’re not limited to only using SAML – you can combine it with something like OAuth to target a wider market.
OAuth 2.0
OAuth 2.0 is a standard protocol for identity authorization. It’s mostly used in organizations where the employees use native applications (mobile and desktop apps). Unlike SAML 2.0, it’s not dependent on the browser to log the user into different applications.
In OAuth 2.0 based SSOs, the most common workflow is a little different compared to SAML-based SSOs. In these SSOs, the client is called one additional time. Here’s how it works:
When a user tries to gain access to an app, the app initiates an authorization grant (a temporary code used for gaining an access token).
The identity provider (SSO) issues an access token after receiving the authorization grant.
The app receives the access token and contacts the SSO provider again.
The SSO provider confirms the user’s identity, and the user is allowed access to the app.
OpenID Connect
OpenID Connect (OIDC) is an identity layer on top of OAuth 2.0. It operates like SAML (through authentication tokens and requests). By placing an identity layer on OAuth 2.0, it helps users cater to web-based applications as well as native applications. As opposed to SAML 2.0 which uses tokens, the information here is exchanged in JSON (JavaScript Object Notation), another format for storing data.
Pros and cons of SSO
We wouldn’t be us if we didn’t weigh the positives and negatives of every tool in our stack, let alone the options we recommend. Here are our top pros and cons.
SSO is a flexible identity management technology that can be configured with other authentication methods such as two-factor authentication (2FA), or multi-factor authentication (MFA). A single source of authentication and user identity management, is SSO too good to be true? Check out our pros and cons below:
Pros of SSO | Cons of SSO |
|---|---|
Pros of SSO | |
Centralized multi-system management | System lockout if SSO goes down |
Cons of SSO | |
Improved user experience and productivity | Single point of failure in case of breach |
Reduced strain on IT and Dev resources | Single point of entry in case of breach |
Increased security and compliance |
SSO pros
We love SSO and think it’s a must for organizations operating online. Let’s look at why.
Centralized multi-system management
Access control for applications can be managed centrally by administrators. Users can be grouped in the identity provider with managed permissions. Access to certain applications can be granted to groups or individual end users.
Improved user experience and productivity
The quickest way to increasing productivity is the path of least resistance. And there’s nothing that takes less time than one touch access. SSO makes user access as easy as opening downloaded applications on your desktop.
Reduced strain on IT and Dev resources
SSO also makes life easier for IT. They receive fewer requests for password resets and recovery for multiple apps every week. SSO simplifies revoking access to all a user’s accounts in one fell swoop in case an account is compromised, or an employee leaves the organization.
IdPs reduce, or eliminate, the need for spending dev resources on constructing security management programs in-house. With the configurable nature of SAML and SSO solutions, outsourcing these services are a practical decision with scalable benefits.
Increased security and compliance
SSO is a security focused solution that is configurable and scalable. While it is not currently explicitly required in regulations like GDPR or CPAA, it does make implementing the security standards outlined by those regulations much easier. SSO is built to be adaptable, allowing you to incorporate other security methods such as 2FA as required – and make updates quickly across your company as regulations evolve.
SSO cons
And what about the cons? Ironically, there are a few security things to keep in mind if you’re considering implementing single sign-on.
Restricted access in an outage
One of the biggest disadvantages of SSO is that when you log out of one app, you log out of all. Also, if your SSO service is down, you’re locked out of your services, even if all your apps are up and running.
Single point of failure
By being the primary source of identity verification in your organization, SSO also becomes a single point of failure. If attackers get to your SSO solutions provider, all your company data will be at risk.
Single point of entry
A single point of failure also means a single point of entry for security risks. If one employee’s SSO credentials are compromised, an external threat could very quickly gain access to your entire stack. But, let’s be honest –, that truth is valid even if SSO is not a part of your solution. A compromised password is a compromised password.
The latest authentication techniques such as WebAuthN, Yubikeys, biometrics, etc. are easy to integrate into SSO, and these advanced authentication techniques may not be supported by smaller service providers.
Top SSO vendors
Even though SSO protocols are relatively stable and consistent, there are many SSO providers out there offering slight variations in features, cost, and support. Let’s take a look at a few industry leaders:
Okta
Okta supports secure password management, authentication, and authorization for your apps and services. It is customizable and scalable for evolving security programs, and offers an additional layer of security with its ThreatInsights feature that detects malicious IPs across Oktas own customer base.
Okta supports 7,000+ on-premise and cloud apps.
Some of Okta’s customers reported a 600% ROI.
Okta supports 25 languages around the globe.
You can start using Okta’s SSO for $2 per user per month.
Auth0
Auth0 provides authorization and authentication but, historically, is a more developer- focused IdP and may be more flexible and configurable for SMB companies or companies in their startup phase.
Auth0 supports 15 pre-integrated cloud-based apps.
Auth0 boasts of a 548% ROI in less than six months.
They support 39 languages.
They have a free plan that supports up to 7,000 users.
OneLogin
OneLogin is comparable to Okta and features easy password generation, a transparent subscription plan, extensive knowledge base and customer onboarding, and expanded global support services.
OneLogin is a global SSO provider that offers support for 21 languages around the globe.
They support 6,000 pre-integrated apps.
They claim you can get a 482% ROI by using their identity services.
OneLogin’s SSO also costs $2 per user per month.
If you’re in the market for an SSO provider, check out the user reviews for all three as well as Azure AD SSO, Ping Identity, and AWS SSO.
What types of companies should implement SSO?
SSO for all.
IdPs solve problems for a variety of use cases – from individuals wanting to manage their personal credentials to companies at all scales. But is particularly useful for these types of organizations:
Remote/hybrid SaaS companies
Companies that have a large portion of their employees working remotely can reduce risks and improve cybersecurity by using SSO in addition to two-factor or multi-factor authentication. Employees logging in from home will have to authenticate their credentials to gain access to the company’s technology stack. Multi-factor authentication will ensure that employee credentials are not misused, and the IT help desk will have the ability to revoke access in case an employee’s credentials are compromised.
Bad actors are always trying to find ways around simple multi-factor authentication with phishing attacks. Hardware tokens and biometric security measures, like YubiKeys leveraging the FIDO2 protocol, help mitigate attacks. Check out how our team stopped a large-scale phishing attack.
Companies with extensive technology stacks
Companies that work with a lot of apps and tools can provide a seamless experience for accessing these apps through SSO. These companies can also eliminate the chances of employees being locked out of different apps due to lost credentials.
Why Mailgun implemented SSO
We’re not just here to feed you a 2000 word sermon on why you should consider SSO.
We do as we preach. Mailgun uses SSO internally to manage our own teams, services, and applications. It’s one of the many ways we keep our data and systems protected.
SSO means ease-of-integration for companies to manage their user identities with their preferred IdP. So, when our user community requested that we implemented SAML single sign-on, it really was an obvious choice.
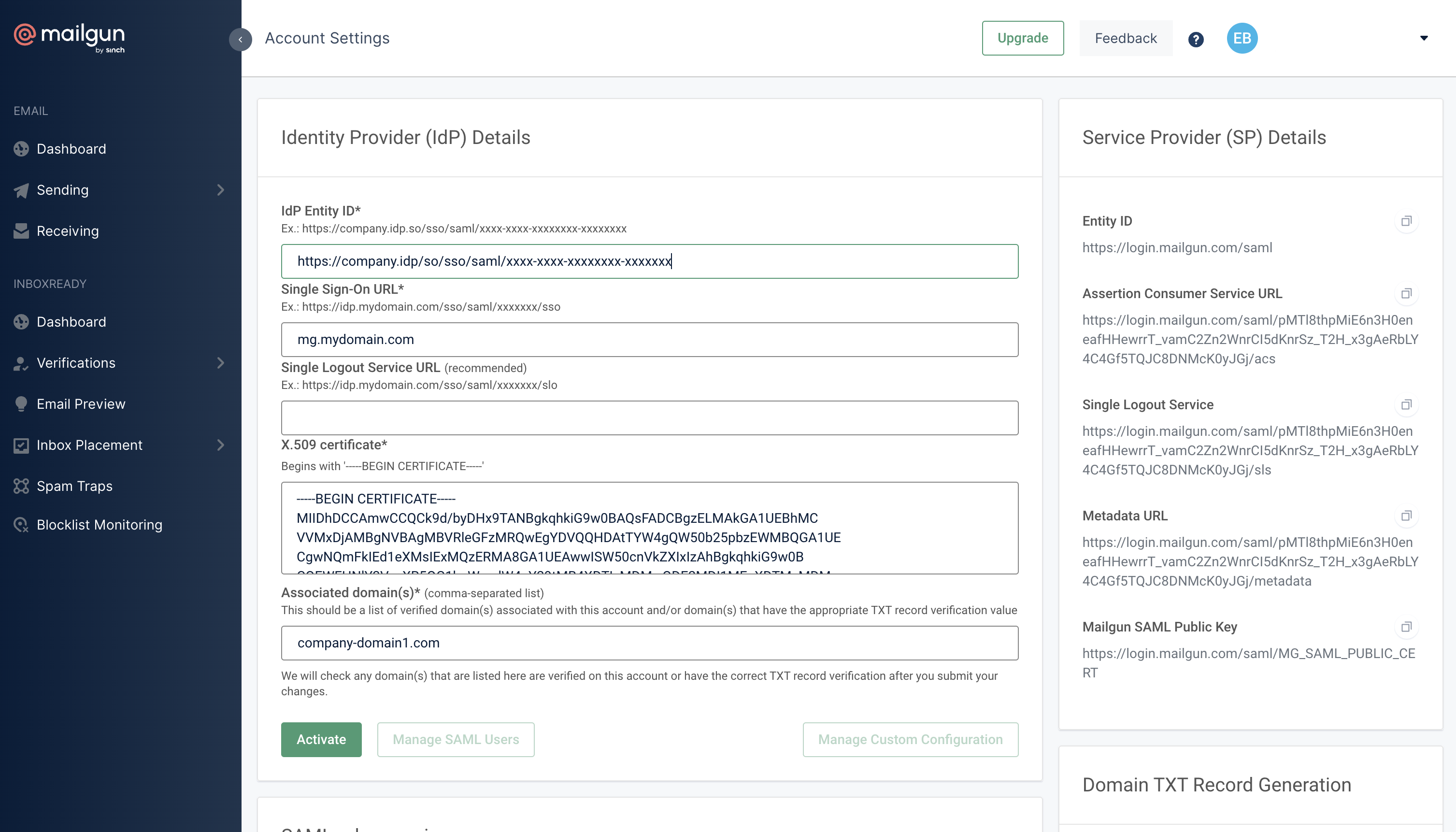
Integrating with your IdP to authenticate users via SSO is simple. To get started, you’ll just need to configure SAML within your Mailgun account for a verified domain and follow the instructions in our detailed SAML SSO documentation.
You made it to the end
This was a long one but we hope it helped.
At Mailgun, we’re always driven by our desire to make our product as usable and accessible as possible, and SSO plays a big role in achieving this. With remote work and the growth of cloud-based solutions, “one ring” to rule your access management is an easy way to integrate and scale complex security. Just make sure that your one ring supports biometrics.
We’re nerds when it comes to security. Don’t believe us? Check out our ebook for the deep dive you didn’t know you were missing.
Learn about email security and compliance
Email security and compliance
Email security isn't easy. But you need to protect your business, brand, employees, and subscribers. Find out about the benefits of continually improving email security and compliance from our industry experts. It's yours to explore. No form filling required.







