Deliverability
Email Scams: How to spot and avoid them
Email scams come in many forms and target your personal information and reputation. Once you understand how scammers operate, you can better identify and avoid being victimized by scammers.
PUBLISHED ON
Not to be dramatic but falling victim to email scams can destroy a person’s life, cripple a business, cost millions of dollars, and waste countless hours of time. The worst part is you may not know you’re being victimized. An email scammer can sneak into your digital life undetected, and sit there collecting your data, watching your digital activities for months.
In this article, we’re exploring common types of email scams in-depth so you can learn how popular scams work, how to spot them, how to protect yourself, and what to do if you realize you've been victimized.
Table of content
Phishing
Doxing
Botnets
Advance fee fraud
419 foreign money exchange scams
Trojan Horse email
What is malware?
Virus-generated imposter emails
Supply chain attacks
Slow loris
Subscription bombing
Table of content
What are email scams?
Broadly speaking, email scams attempt to trick people into doing things that cause them harm for the benefit the scammer sending the email.
In the early days of email, scams were easy to spot. They featured terrible grammar, bad spelling, bizarre names, and crazy-looking sender addresses. Classically, a Nigerian prince was featured somewhere in the story.
While you still see some of that today, the real threats lie waiting in newer types of email scams, including the ones we’ll be exploring in this article.
Email scam glossary
We’re focusing on three common types of email scams: phishing, doxing, and botnets.
Phishing
The classic bait and hook, a phishing attempt is a scam email that aims to extract personal information from the recipient by tricking them into believing the email is from a person or company they trust.
Phishing messages usually include a link to a fake website that looks legitimate, where you are asked to enter credentials such as passwords, credit card numbers, or account information. Other phishing messages include attachments or links that upload malware to your device when clicked. You may not realize you’ve been infected because the malware simply operates in the background syphoning your information.

In July 2022, Mailgun and other companies in the digital communications space became the targets of a large-scale phishing attack.
Some specific types of phishing attacks include:
1. Login scams
Login scams try to trick you into “proving” you’re you. These email scams often declare that your password has expired or been reset and that you need to log in to regain access to your account. The emails will include logos and other deceptive design elements that mimic the real company they are impersonating.
When you click the link within these emails, it takes you to a spoof landing page or web page designed to capture your login information and hand it to the email scammers, who will use it against you later.
2. Fake invoice scams
This type of phishing email targets you financially, and will send a fake invoice, fake shipping notice, or some other graphic that mimics a real company like Amazon, Netflix, or PayPal. The message plays on your fears by creating a sense of urgency; claiming your account is closed or that it has been breached by a hacker, and that to solve the problem you need to verify your account information or relink your bank account.
It’s all a lie. Giving up your account information means giving in to the scammers.
3. Google Docs scam
If an email scammer gets a hold of an email address from someone you trust, like a co-worker or friend, they may send you an email that includes a Google Docs link. Once again, it’s not really a Google Docs link, and if you click on it, malware will likely be uploaded to your computer.
4. Government scams
Email scammers may also attempt to impersonate a government agency to collect sensitive information like social security numbers and other personal data. The email will resemble something from a real government office and will include fake links or attachments.
Risks of email phishing scams
Behind all these email scams, you face similar risks.
Scammers want your money, your information, or control of your device. Depending on the scam, you could become a victim of identity theft. They might use your information to open accounts in your name, get cash advances, or threaten you. If you’re lucky, they may just steal your money or sell your information to someone else.
How to spot email phishing scams
You may already have anti-phishing protections in place. Companies like Google will scan incoming email messages for potential threats, and issue warnings if they somehow manage to miss the spam folder. Aside from a bright warning banner, the simplest way to expose a suspicious email is to hover over the from address. A mismatch between the sender’s name and email address is a dead giveaway, especially if the email is imitating a real company.
Other warning signs might show up as slight alterations from the real company’s brand, such as:
The use of .con instead of .com
Numbers in place of letters, such as Linked1n
The use of .org instead of .com, such as paypal.org
Dashes instead of dots, such as mailgun-com
Extra letters, such as gooogle, or netfllix, also known as cousin domains
A whole string of bizarre characters
If the sender’s name and address seem correct, you can use a similar approach to examine the landing page URL, which you should be able to see by hovering over the link without clicking on it. A scam URL will be altered with strategies similar to those in the above list.
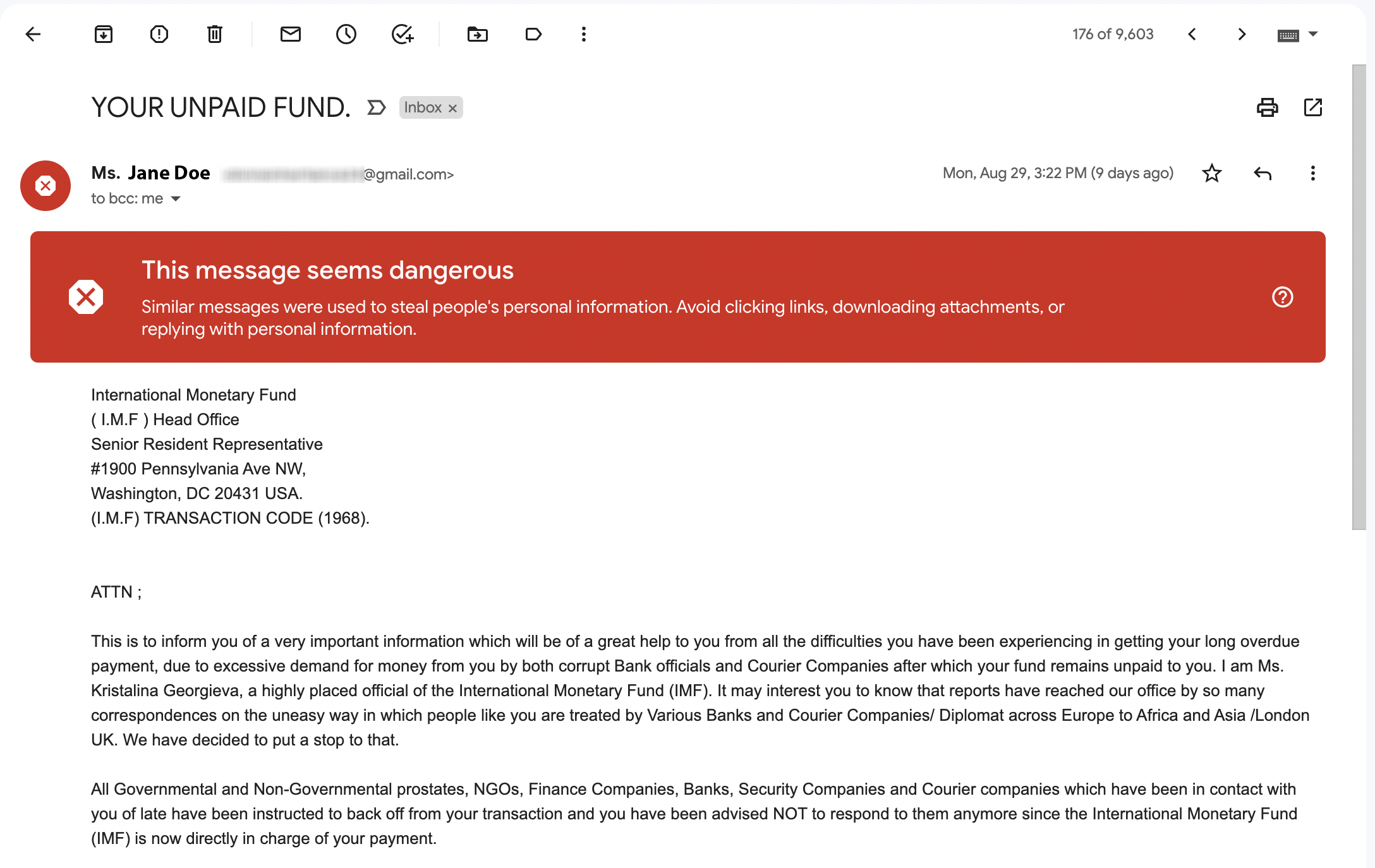
Remember, real problems with your bank account or service would alert you directly through that service or institution, or at the very least through an email with accurate company and personal information. In other words, if the email greets you as ‘sir’ or ‘madam’ or some other generic greeting, but then asks you to log in and fix your account, that’s a major red flag. We’ve got personal experience successfully mitigating phishing scams. Check out how we did it.
More sophisticated but surefire strategies for spotting phishing emails include verifying email authentication protocols such as SPF, DKIM, and DMARC. If email authentication isn’t already in your wheelhouse, resources like MXToolbox make it easy to parse headers and show anti-spam data as well as other diagnostic details.
Overall, it’s extremely rare for legitimate companies to ever ask for personal or account information over email. They just don’t do it. So be suspicious of any emails that do, they’re likely fraudulent.
How to avoid email phishing scams
Spotting phishing emails is good. Avoiding scams altogether is better. Here are a few strategies:
Use email authentication protocols (Listen to a podcast about how DMARC fights phishing emails).
Don’t give out account numbers or personal information to unsolicited email requests.
Only visit secure sites that use https, as opposed to http.
Contact the company directly and confirm they sent the email.
Don’t open suspicious emails from unknown senders.
Report all scam emails as spam to your internet service provider.
Use a password generator and manager to employ hard-to-guess passwords.
Use antivirus software.
Install a virtual private network (VPN).
Use 2FA security that requires you to enter a code from a secondary device or verifying text message.
Doxing
Doxing is when someone intentionally searches for and exposes your personal information online – whether physical or digital information – with the express purpose of destroying your reputation. When you get doxed, your private information becomes public and anyone can use it against you.
Risks of being doxed
If your physical address were to be doxed, it would mean mailing things to you that are illegal and then calling the police, or phoning in a fake crime at your house. When the doxed information is digital, such as login information, anyone can then use that to manipulate your accounts or damage your online reputation for personal gain.
Doxing is malicious and intentional. Not random. It’s also a fast-track way to do what many phishing scams attempt to do, and its goal is ultimately the same. It’s about getting your personal or financial information and converting it to dollars in the scammer’s pockets.
How to spot doxing
You’re getting doxed if you start getting threatening messages that include information about you people shouldn’t have. The people doing the doxing want you to know they’re targeting you.
How to avoid getting doxed over email
Doxing involves much more than just email, but sometimes email can be the source of information malicious parties use to exploit you.
Here are just a few tips to avoid getting doxed:
Don’t share personal information online, even with friends.
Get a VPN to protect your IP address from public exposure and to encrypt your online activities.
Use strong passwords, and don’t reuse passwords on multiple sites.
Use different email accounts for different purposes, such as personal, professional, and commercial accounts.
Be wary of downloading mobile apps, especially when they ask for access to personal information they shouldn’t need.
Tip: Email providers such as Gmail provide you with unlimited email address variations. Subscribing to a newsletter? Try adding +newsletter to your address: youremail+newsletter@gmail.com. This not only lets you organize your inbox but gives you a better log of where and when your email was compromised, and how your data is being managed.
Mobile apps are becoming one of the most common methods for uploading malware to devices. How does that relate to doxing? Malware often tracks your movements, logs, and reveals any data or activities you collect or perform. Later, this can be used against you in a dox attack, as well as in other types of scams. The more information channels we add across devices, the more opportunities there are for that data to be compromised. Healthy data practices can reduce your risk of being targeted for scams.
Botnets
A botnet is a network of personal computers that have been infected with malware. The malware gives control of the network to a scammer. In most cases, the individual computer owners have no idea their devices are being used to commit crimes.
With enough computers under their control, the scammer or hacker can initiate large scale assaults on big companies (botnet attacks) compromising troves of customer or patient information and preventing that company from operating securely.
In terms of email, botnets can turn each computer under their control into a mini email server. Then, using all these combined servers, they can start sending phishing emails in large quantities. Unlike conventional phishing scams, botnet email spam can’t be combatted as easily because each email will come from a different computer ‘server’ within the botnet.
Botnets using this strategy can be very hard to spot and remove. You can take out one computer, but if the botnet has 500,000 under their control, losing a handful now and then doesn’t make a dent.
Risks of being part of a botnet
Being part of a botnet means the scammer has control of your computer. In theory, this means they could monitor your digital activities, collect passwords and other sensitive information.
Even if they’re just using your computer to break into a larger company or send out email spam en masse, being in a botnet could damage your sender reputation by getting you flagged as a spammer and blocklisted.
How to spot a botnet
If a botnet is attacking your IP or email in some way, a good indicator is that you keep seeing similar messages appearing in your inbox (or your employees��’ inboxes), but each time the emails are from different senders.
If your computer is part of a botnet, one way to find out is to check your IP address on a site such as Sonic Wall. This isn’t foolproof, as new botnets won’t be in their system yet, but these sites have good information about all known botnets.
How to avoid botnets
The first step to avoid botnet scams is to understand them. The next step is to keep your domain-based reputation strong. Email authentication protocols like DKIM, SPF, and DMARC help you stay on top of security and protect you from accidentally uploading the malware that will make your computer part of a botnet.
When it comes to security best practices, don’t click on suspicious links, email or otherwise. This includes links from unknown sources on social media, less reputable websites, and invasive online ads. Good antivirus software also stays up to date on the latest botnets and can identify any malware on your devices. Learn advanced methods for email security here.
Tip: Change your passwords regularly. Password managers make this easier and allow you to create complex passwords without needing to memorize them.
Beyond phishing, botnets, and doxing, there are additional email scams that have unique characteristics, though they bear some similarities to the ones we’ve already discussed. Here are a few:
Advance fee fraud
This email scam attempts to convince you that you’ve won a prize, received a grant or loan, been invited to an event, or gained another benefit. But to claim it, you must pay some sort of fee, usually involving a wire transfer or gift card.
If you get duped and pay the fee, expect that some other complication will arise that delays your benefit. The scammers will string you along for a while and then vanish when they think you’re about to stop paying their fees.
There’s no infallible way to block these types of emails because most of the time they’re direct emails, often from webmail. Thus, it falls on the recipient to recognize the scam for what it is.
If something is too good to be true, it usually is. Common sense should prevail here. Why would a random person email you about something so personal or seemingly important? They wouldn’t. Don’t fall for it — delete the email, report it as spam, and you’ll be fine.
419 foreign money exchange scams
419 scams are a variation on the advance fee fraud but bear special mention because of their notoriety. The 419 scam artist will claim to know someone of great wealth who recently died with no heirs, and if you can help them access the money, you will get a cut.
Historically, these scams originate from Nigeria, and 419 is the Nigerian penal code for fraud. The mechanics of a 419 scam follow the same protocol of other advance fee frauds.
Trojan Horse email
This scam may sound familiar from the movies. The Trojan Horse is a hack that gets its name from a Greek myth where a large wooden horse was given as a gift to the city of Troy by the Greeks. Inside the horse was a small army, which emerged during the night, opened the gate for the rest of their army, and conquered the city.
In a Trojan Horse email, the email captures your curiosity using something like a silly joke, downloadable tickets, a must-see photo, or a software patch to protect your computer from viruses.
No matter the gift being offered, it�’s just a ruse to get you to open an attachment, which then uploads malware to your computer.
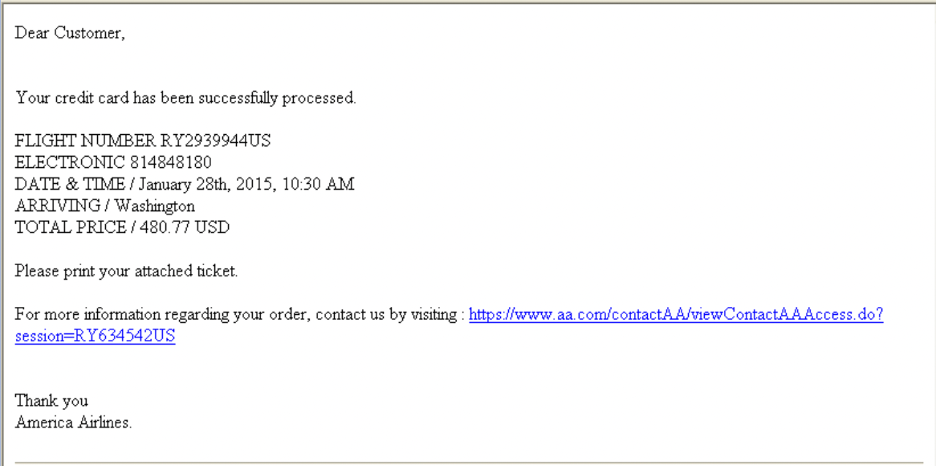
The common feature of all Trojan Horse email scams is the attachment. Whenever an email from an unknown sender tries to persuade you to open an attachment, be suspicious. That’s your best defense.
What is malware?
Malware, or malicious software, comes in all sorts of varieties, from ransomware that locks down your computer until you pay, to programs working in the background for a botnet, to monitoring your activities and keystrokes, and so much more. Unfortunately, email is a common vehicle for transmitting malware, but that doesn’t mean you’re defenseless. There are several things you can do to secure your email gateways.
As you’re probably noticing, email scam types have a lot of overlap. A phishing email might be a Trojan Horse, for example, with the goal of uploading malware to make your computer part of a botnet. That’s why the risks to you, the ways to spot them, and the ways to avoid these email scams tend to be similar.
Virus-generated imposter emails
This email scam is particularly insidious and much harder to spot.
Here, the scammer first gains access to one computer using malware that enables them to see someone’s email contact list. Then, they use the malware to impersonate that individual and send a bulk email to their contacts.
Unlike typical phishing scams, these emails appear to be from a trusted sender. Thus, the link or the attachment they want you to click or open is that much harder to resist.
The only thing you can do with these is to always be vigilant and alert when opening emails. Even if you trust the sender, don’t open the email, or click attachments if they make an odd request, or if the way it’s written just doesn’t sound like the person they’re impersonating.
Suspect someone you know may have been hacked? Call them – don’t email – and verify that they really did send you an email.
Supply chain attacks
Supply chain email scams target businesses, and the goal is to get the contact information of all their customers. The tactics could include many of the scams you’ve already seen – phishing, botnets, Trojan Horses, virus-generated emails, etc.
The difference here is who is being targeted.
Usually, a big company with a massive customer database is the ultimate target. But because that company has robust cybersecurity, the scammers will target a much smaller business that is far down the supply chain of the big company.
Once they break into that smaller company, they’ll send emails that appear to be from the smaller company to certain people who work at the larger one. All it takes is one person at the big company to open the scam email, and all the company’s data could be at risk.
How do you stop these?
It’s up to the company to train their employees to be suspicious of emails claiming to be from one of their supply chain partners. Many large companies can involve dozens or hundreds of smaller companies along their supply chain and verifying email legitimacy will be up to many people at each link on the chain. Automating and managing these communications can help.
Slow loris
This is less an email scam than it is strategy. A slow loris targets dedicated IPs and is basically the cybercriminal’s version of ‘warming up’ an IP, which is something legitimate companies can do when they launch a new IP address for email marketing purposes. A new IP has no email sender reputation, so you can warm it up by keeping your send volumes low at first and increasing them over time.
A slow loris uses a similar process to increase their sender reputation. Then, once they reach a certain point of credibility, they blast out huge volumes of spam and flood far more inboxes by getting past spam filters.
Your best defense against a slow loris spam assault is to use email authentication protocols like DKIM, SPF, and especially DMARC, as well as robust spam filters, which will help keep more of these spam emails out of your inbox.
Subscription bombing
Subscription bombing is the email-centric little brother of doxing.
First, the scammer must acquire your email address somehow either by scrapping it off a website or buying an email list. Once they do, they can create a bot that will subscribe you to hundreds of websites using their email opt-in forms. Once that happens, your inbox explodes with hundreds or even thousands of emails from all the websites. You’re getting their welcome series and ongoing email marketing, except you didn’t ask for it.
The result is mostly annoyance because you must go through and unsubscribe from all these sites, and more may continue coming in. Another problem with this is that with all these useless emails coming in, you increase the risk of missing emails that are important, and increase the risk of clicking on a malicious link accidentally.
Subscription bombing is personal, like doxing, and is usually done intentionally to make your digital life more complicated. Companies can reduce the likelihood of being implicated in a subscription bomb by requiring double opt-ins for their subscribers and putting account verification processes in place.
What to do if you receive an email scam
Now that you know how to identify email scams and protect yourself, all that’s left is to dispose of these messages. Reporting scams helps identify and stop them – or at least slow scammers down. We recommend reporting to:
The government: Use the Federal Trade Commission’s fraud email address – spam@uce.gov or visit the FTC website for more information.
The email service provider: If the email came through Mailgun, you can send the message headers to abuse@mailgun.com, and we will take it from there.
The company being targeted: Go a step further and inform the brand being impersonated if you’ve received a phishing scam, as well as the email service provider, such as Sinch Mailgun. If you get doxed, report the doxing attack to the platform where your information has been exposed.
Remember, don’t click, don’t open, and don’t reply. Once you’ve verified the email is a scam report it, delete it, and frequently clear your email trash and spam folders.
Keep your email program safe with Mailgun
Sending a simple message can be a simple task, but we’ve just described how simple messages can cause damage in a big way. Email scams aren’t likely to disappear anytime soon. As scammer’s tactics evolve, so do our defenses. Working with an ESP (like us) can help you stay ahead of the game and ensure your messages aren’t mistaken for scam emails as security protocols advance.
Staying on the right side of email is our specialty. Get started with a free Mailgun account and keep your email system and subscribers secure.






